
Table of Content
- The Consequences of Cyber Attack
- Hacker Apocalypse
- It’s Coming Home
- Introducing WatchGuard
- Multi-Factor Authentication
- Don’t Click That Link
- Invest in Security Software
- Training Training Training
- Encryption is Key
- Watch Your Employees
A couple of years ago, a friend of mine, a young versatile entrepreneur, had launched a revolutionary financial product to bridge the credit gap for the unbanked. His product gained incredible traction in the first year with over 100,000 users downloading the app and a million naira in processing.
Unfortunately, a chink was found in the company’s armoury unexpectedly halting my friend’s upward trajectory. The company’s database was hacked, wiping out its entire financial records and customer base.
What is a Cyber Attack?
A cyberattack is an attempt to steal, alter, or destroy a specified target by hacking into a susceptible system. According to Wikipedia, cyberattacks can range from installing spyware on a personal computer to attempting to destroy the infrastructure of entire nations.
The Consequences of CyberAttack
Twenty one years into a much more digitized century, a million and one online tools have popped up for big and small companies to optimize regular work processes with.
The cost incurred from a cyberattack or a data breach is mind-blowing. According to a report from Atlas VPN, over $1trillion (N504 trillion) was spent on cybersecurity or given up as a result of a cyberattack in 2020 (this cost was exacerbated by the COVID 19 pandemic).
And this is not abating any time soon. Cybersecurity Ventures, a cybersecurity research firm, expects global cybercrime costs to grow by 15 per cent per year over the next five years, reaching $10.5 trillion annually by 2025 (more than 10x the expected GDP of Nigeria in 2025).
Hackerpocalypse
These staggering stats only point to one thing; companies all over the world are losing the cyberwar to hackers, most especially small and medium-sized corporations where it is estimated that 60 per cent go out of business within six months of falling victim to a data breach or cyber attack.
Already, 1 in 6 companies pays a ransom to hackers according to the annual Hiscox Cyber Readiness Report.
READ: Top Reports On Data Security Issues In 2020
It’s Coming Home
Back home in Nigeria, the statistics are grim as well. According to a British software and hardware company report, Nigerian companies recorded the second-highest percentage (86% were targeted by hackers) of cyberattacks worldwide behind India last year. In 2019, a report by Serianu, an IT Services and Consulting firm, Nigeria lost $649 million (N327.1 billion) to cybercrime.
This shows that Nigeria, and in extension, Africa isn’t insulated from this ongoing cyberwar. Africa is increasingly the target of cyber espionage, making it imperative for businesses across the continent to find effective ways to protect their assets from would-be hackers.
Introducing WatchGuard
Founded with a vision to make enterprise-grade security accessible to businesses of all sizes, WatchGuard has consistently pioneered innovations that empower organizations to navigate the digital realm with confidence. Their suite of solutions is meticulously crafted to address the multifaceted challenges posed by modern cyber threats. From advanced firewall protection that acts as the first line of defense against intrusions to secure Wi-Fi connectivity solutions that ensure safe data transmission, WatchGuard’s offerings are designed to fortify businesses at every touchpoint.
Furthermore, WatchGuard’s commitment to excellence extends beyond mere product offerings. They continuously invest in research and development, staying abreast of emerging threats and evolving security paradigms. Their holistic approach to cybersecurity encompasses not just proactive threat detection but also actionable insights, empowering businesses to preemptively address vulnerabilities before they escalate into full-blown breaches.
In essence, WatchGuard is more than just a cybersecurity provider; it’s a strategic ally, a guardian that stands sentinel, ensuring that businesses can harness the power of the digital age without compromising on security. As we delve deeper into this article, we will explore six pivotal ways WatchGuard’s comprehensive solutions can serve as the linchpin of your organization’s cybersecurity strategy, fortifying your defenses and ushering in a new era of digital resilience.
Here are 6 easy ways businesses can avoid being hacked:
1. Multi-Factor Authentication
The easiest and most popular way to breach a company’s backend is through password theft. According to a 2020 Verizon data report, 81% of the total number of breaches leveraged stolen or weak passwords. Also, in a breach report done in 2019, over 1 million passwords are stolen every day. What’s worse is most hackers do the bare minimum to hack these passwords. When it comes to password security, all a hacker needs is an employee’s insistence on being the weak link (you know what they say about the weakest link?).
Thank goodness there are ways a company can guard against such monstrous vulnerabilities and one of them is the use of Multifactor Authentication like Google and Microsoft Authenticator to help stave off would-be snoopers. In addition, employers can put in place second-level security protection like tokens and biometrics for their employees.
2. Don’t Click That Link

Employees are daily bombarded with emails, but quite a lot of them are intended to steal sensitive information. This is called phishing, which tricks victims into revealing vital and personal information to the attacker. Phishing attacks are increasingly becoming the norm. A 2019 Verizon Data Breach Investigation Report estimated that 94% of malware are delivered via email while in a 2019 report done by Symantec Internet Security Threat Report, 48% of email attacks are office files.
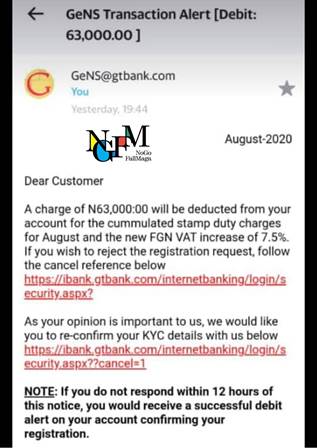
This makes it imperative for businesses to adopt anti-phishing strategies to guard against regular phishing attacks. Some of these strategies could include using more sophisticated anti-phishing filters, user training for employees to recognize phishing attempts and deal with them immediately, setting up firewalls and security measures.
Most importantly, employees and business owners should learn NOT to click on a link or download any file until sure!
3. Invest in Security Software

Investing in cybersecurity software and firms is a no-brainer for businesses and organizations looking for a holistic approach to protect their data, especially in a year where global spending on cybersecurity is expected to exceed $1 trillion. This is more pertinent for small businesses as they are more prone to data breaches.
A trusted anti-spyware will limit a company’s exposure to snoopers by quickly detecting malicious applications.
4. Training Training Training!
You can spend all the gazillion dollars you have on anti-spyware software but if your employees aren’t versatile enough to quickly detect or identify malicious links or are careless with their company’s credentials, your business will always be susceptible to cyberattacks.
According to an IBM study, over 95% of cybersecurity breaches are due to non-IT-related human error. This means for every 10 breaches that occur in a company, only 0.5 are due to non-human error.
This makes training of employees in basic cybersecurity very imperative. Employees must understand what a malicious attack looks like and must be careful enough not to disclose confidential details to third parties.
5. Encryption is the Key
Except you are trying to cyber spy on North Korea or into the espionage business in general, you don’t need high-level complex encryption to protect your business from cyber-attacks. However, you still need standard level encryption for your data and entire work process to keep the low life, online snoopers, away.
If you don’t already know, encryption is the process of converting information or data into a code, especially to prevent unauthorized access. Encryption plays its most important role when two parties intend to exchange confidential information across digital platforms.
Think of it as Harry Potter’s invisibility cloak or switching on stealth mode in the middle of a splinter cell mission. Your messages will travel right through the noses of ill-intentioned parties and stay undetected.
6. Watch Your Employees!
Your employees are the heartbeat of the company. On the flip side, they can also act as the death knell to a company by contributing, either deliberately or inadvertently, to its downfall through cyberattacks.
To guard against this, avoid/limit the sharing of very sensitive data to your staff. If you must share this data, ensure you plug all potential leakages. If possible, create a sort of ‘Watch System’ for your staff, but this must not impugn their rights to privacy.
Most importantly, put a premium on employing the right and trusted person who will do nothing to sabotage your business which includes subjecting it to cyber hacks.
Conclusion
In wrapping up, it’s essential to confront a stark reality: can your business endure a cyberattack without crumbling in its wake? If your response leans towards uncertainty or hesitant affirmation, it’s time to consider implementing the cybersecurity solutions highlighted in this article. Fortunately, all these solutions are within reach, courtesy of WatchGuard. Their expansive range of offerings equips businesses with the formidable defenses needed amidst today’s unpredictable digital landscape. As you navigate your organization’s cybersecurity trajectory, recognize that choosing WatchGuard means more than embracing technology; it signifies an investment in tranquility, resilience, and envisioning a future where your enterprise flourishes, untouched by the perils of cyber threats.
Don’t leave your business’s security to chance. Click here to discover how WatchGuard can tailor a solution to fit your specific needs and fortify your defenses against cyber threats. Your business’s future deserves the best protection.
