As a business owner, the cost of not investing in cybersecurity is huge. It’s like leaving your car keys on the ignition with your car doors open in a car park while shopping a few kilometres away. It is estimated that over $6 trillion will be lost annually to cybercrime from 2021. That’s more than the proceeds made from the global trade of all major illegal drugs combined.
Table of Content
- Importance of Cybersecurity Software
- Barracuda Spam Firewall
- Fortinet Security Fabric
- Google Cloud Security
- Intruder
- Syxsense Secure
- Proofpoint Email Security
- Acunetix
- Cisco Application – First Security
- Netsparker
- Sophos
- Vipre
- Norton Security
Importance of Cybersecurity Software
You might be thinking that hackers in this clime are not as sophisticated as their destructive peers worldwide. Think again! In the last 10 years, Nigeria has lost up to N5.5trillion ($9.7 billion), that’s an average of N550 billion ($9.7 million) every year! Also, Nigerian companies recorded the second-highest percentage (86%) of cyberattacks worldwide behind India last year.
These staggering and scary statistics show that Nigerian businesses are far from immune to cyberattacks, let alone get attacked. This is why companies must set aside not so large a chunk of money to invest in standard cybersecurity software. It doesn’t just protect your company’s assets and data from being stolen but gives your business a fighting chance to last far longer as 60% of small businesses are expected to go out of business within six months of falling victim to a data breach or cyberattack.
Here are 12 powerful cybersecurity software products you can invest in to secure your business:
READ MORE: 6-ways-to-keep-hackers-away-from-your-business.
Barracuda Spam Firewall
One of the increasingly popular and obnoxious ways to gain access illegally to sensitive information of a company is through malicious emails. This can be prevented by the use of the Barracuda Spam Firewall. Barracuda is one of the most popular cybersecurity companies in the world with a lot of security products geared towards protecting businesses from internal and external threats.
The Spam firewall, connected to the Barracuda security cloud, scans internal and external emails and incoming files using three layers of powerful virus scanning technology. Integrating this security software with your company’s
Fortinet Security Fabric
Most times, hackers attempt to hack into your system simultaneously from all angles. To prevent this, you will need a complex integrated security system like the Fortinet Security Fabric.
The FSF is a complex ecosystem of security networks that continuously assesses the risks and automatically adjusts to provide comprehensive real-time protection across the digital attack surface and cycle. The FSF is a great security solution for large enterprises with a vast and deep system.
Google Cloud Security
One of the most efficient and intelligent means of protecting your entire digital assets is Google Cloud Security. From businesses with a single asset like a YouTube channel to businesses with multiple digital assets, Google Cloud Security guarantees the topmost security.
Google Cloud Security quickly detects and halts cyber threats by deploying different solutions which include Security analytics and operations and Web App and API Protection to protect your business from future attacks. Top organizations like Twitter and Evernote have their assets secured with Google Cloud Security.
You can start with Google Cloud Security for free with $300 free credits available for use.
Intruder
Just as the name suggests, the Intruder software is meant to crash the parties of potential hackers by blocking every pathway to an attack. Used by major brands, Intruder is an online vulnerability scanner that finds cyber security weaknesses in a company’s digital infrastructure, to avoid costly data breaches.
It also increases productivity as it frees employees to accomplish other important duties. The cybersecurity company claims to scan as many as 50 potential vulnerabilities delivering comprehensive data that can be used to strengthen the security structure of a company.
The software comes with a 30-day free trial. It also includes three pricing plans; the Essential, Pro and Verified plans.
Syxsense Secure
Another cloud-based vulnerability scanner is the Syxsense Secure which provides end-to-end security scanning and usable insights to prevent cyberattacks from unscrupulous individuals or organizations.
Other features from Syxsense secure include Patch everything; a feature that automatically deploys third-party security patches to secure and support major operating systems, Quarantine Devices to block, isolate and kill infected and malicious processes before they spread, and Collaborate with Ease, a feature that enhances collaboration among the IT and security team.
The key selling point of this cybersecurity solution is the ability to combine all these features into one single cloud console.
Syxsense Secure also comes with a 14-day free trial and two pricing plans which are Syxsense Manage and Syxsense Secure.
Proofpoint Email Security
As earlier alluded to in this article, email remains the most vulnerable source of cyberattack for large and small scale businesses around the world. According to a Trend Micro report, 94% of targeted emails use malicious file attachments as an infection source. Also, 91% of cyberattacks begin with a ‘spear-phishing email, one of the most sophisticated ways cybercriminals steal sensitive information.
Hence, the need for a cybersecurity solution like Proofpoint Email Security which deploys Machine Learning enabled technology to catch both known and unknown threats missed by others.
The software also detects and blocks threats that don’t involve malicious payload, such as impostor email—also known as business email compromise (BEC), a favourite for cybercriminals.
There is no visible pricing on its website, but a contact form is available to fill.
Acunetix
Aside from Google Cloud Security which is arguably the most complete web and API security software out there, Acunetix offers a great option for businesses looking to secure their websites, web applications, and APIs. It also offers actionable insights after performing a deep scan of all web pages and complex web applications.
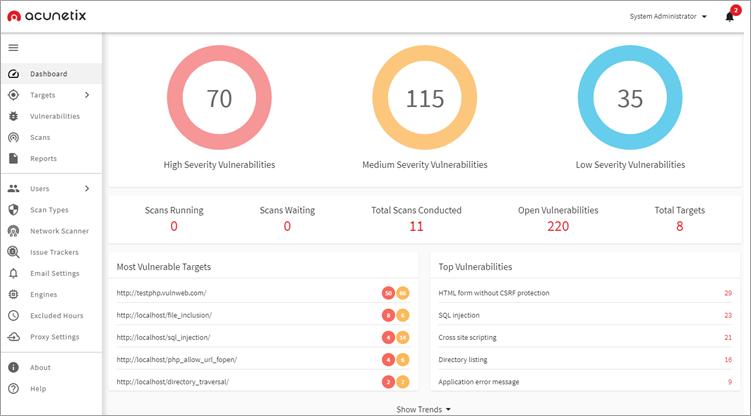
It is an intuitive and easy-to-use solution with functionalities like scheduling full/incremental scans and seamless integration to other software like Azure and Github.
It can be used by both small businesses and large enterprises. It comes in three pricing plans; standard, premium, and Acunetix 360. A demo can be requested.
Cisco Application – First Security
Most cybersecurity companies tend to offer a one size fits all approach for businesses looking to secure their online and offline assets which might not necessarily speak to the latter’s individual security needs. But Cisco Application – First Security offers different layers of cybersecurity approach that is closer, continuous and adaptive.
The different layers or products include Cisco Secure Workload which offers automated protection micro-segmentation based on recommended policies tailored to your applications, Cisco Secure Cloud Analytics which detect and respond to advanced threats across private and public cloud networks, Cisco secure Access which Establish user-device trust and highly secure access to applications, AppDynamics which performs monitoring and deep insight into transaction behaviour and metrics for applications running in public and private cloud environments and finally Cisco Secure Application which prevent and detect application vulnerabilities across your digital business.
The Cisco Application – First security’s adaptability to different cybersecurity needs makes it a go-to choice for big and small enterprises alike.
Netsparker
One of the best cybersecurity automation tools for software companies out there has to be the Netsparker. The tool’s unique dynamic and interactive scanning capabilities are top-notch amongst its peers.

Netsparker offers features and functionalities for automating the security testing throughout the software development life cycle (SDLC). These features save a huge number of hours for team members, identify vulnerabilities that matter, and help security and development teams get ahead of their workload.
Netsparker claims they consistently identify more vulnerabilities and return fewer false positives than other scanning tools.
Another unique offering from the application is its capacity to perform comprehensive scanning while detecting vulnerabilities within a very short time. It also assists developers with actionable feedback that helps them produce more secure code meaning less work for your security team.
As earlier mentioned, the Netsparker tool is incredible for software companies looking to protect their assets throughout the SDLC.
Sophos
Sophos tagline says it all “Sophos stops Ransomware”. Just the kind of messaging that will get companies chomping at the subscribe button.
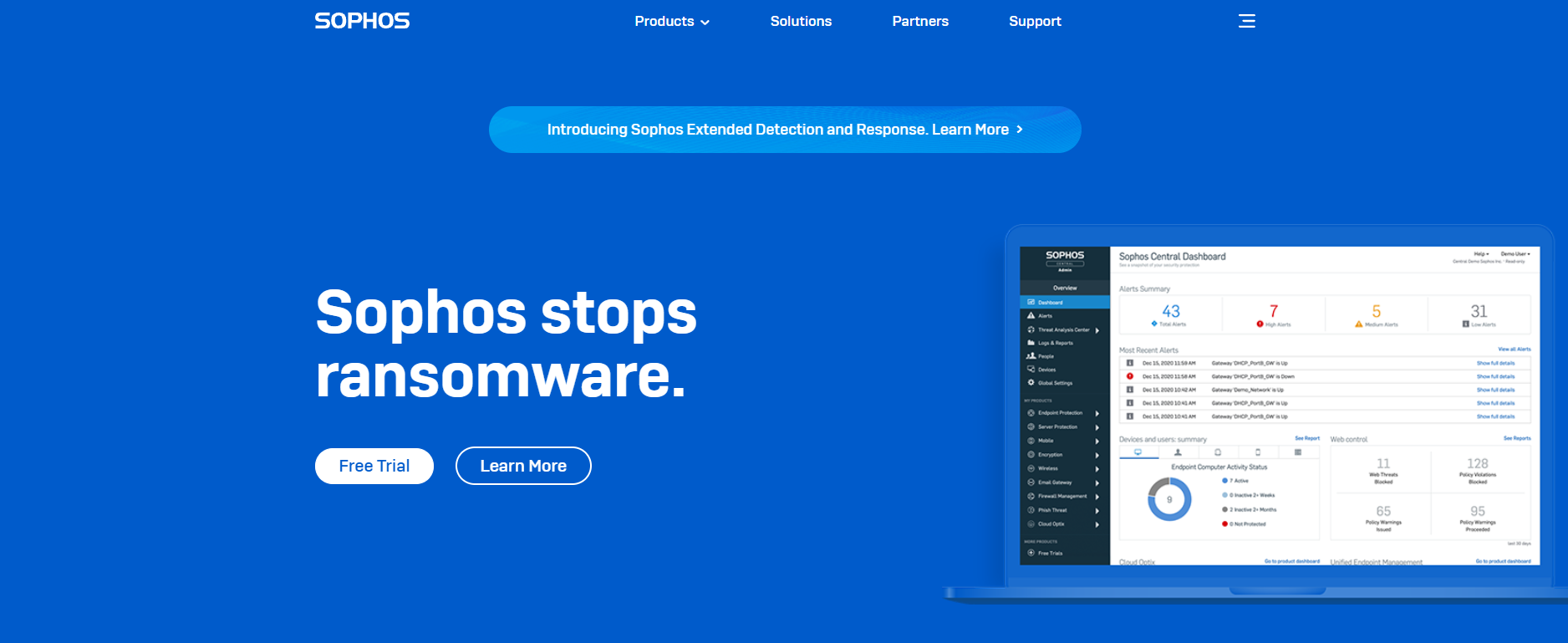
The British-based security software company, through its unique security products, offers protection against known and unknown malware, spyware, intrusions, unwanted applications, spam, policy abuse, and data leakage and also provides a comprehensive network access control to businesses.
Some of these products include Sophos XDR which can intercept and investigate threats across endpoints, servers, firewalls, and other data sources, Sophos MTR which automatically neutralizes the most sophisticated threats, Sophos Cloud Optix, Sophos Emails, Sophos Phish Threat, etc.
A free trial is available for businesses looking to test the waters.
Vipre
Viper is one of the oldest security software companies out there, and like new wine in an old bottle, they’ve been able to adapt to the changing cybersecurity landscape to remain one of the go-to security platforms.
They offer comprehensive layered protections that cater to both personal and business needs. Some of the features Vipre offer include simplified solutions to protect businesses from online threats and data risks, an all-inclusive package and scalable pricing, unparalleled protection for email and endpoint security with the help of AI technology, and a fully integrated solution that is easy to deploy and manage.
Vipre business protection which is suitable for large and medium and small scale enterprises alike is available in three pricing plans i.e. Core Defense ($96 per user per year), Edge Defense ($96 per user per year), and Complete Defense ($144 per user per year).
Norton Security
Norton has evolved over the years from being seen as just an antivirus software to an all-inclusive cybersecurity company. In addition to the aforementioned Antivirus, the company offers different cybersecurity solutions such as Virus Removal, Malware Protection, Cloud Backup, Password Manager, and Secure VPN. It also offers an extra layer of protection for gamers, an interesting distinction from the rest on this list.
Other features include five-layer protection for recognizing and blocking threats, cloud backup services that can store and protect files and documents, a simple, secure, and smart solution for managing passwords, a secure Norton VPN that helps block hackers from seeing what you do online and a series of Norton 360 plans.
Norton is suitable for all businesses looking for top-level digital protection and provides a 30-day free trial for Antivirus while the price for Norton 360 starts at $9.99 for the first 3 months.
Conclusion
It’s digitally suicidal if you don’t have your online assets protected by any of this cybersecurity software on the list. Thankfully, Descasio has got you covered. We’ve partnered with some of these security companies that can comprehensively secure your entire digital assets at the most favourable pricing.